Restarts the operating system on local and remote computers.
Syntax
Restart-Computer
[-WsmanAuthentication ]
[[-ComputerName] ]
[[-Credential]]
[-Force]
[-Wait]
[-Timeout ]
[-For ]
[-Delay ]
[-WhatIf]
[-Confirm]
[]
Description
The Restart-Computer cmdlet restarts the operating system on the local and remote computers.
You can use the parameters of Restart-Computer to run the restart operations, to specify the
authentication levels and alternate credentials, to limit the operations that run at the same time,
and to force an immediate restart.
Starting in Windows PowerShell 3.0, you can wait for the restart to complete before you run the next
command. Specify a waiting time-out and query interval, and wait for particular services to be
available on the restarted computer. This feature makes it practical to use Restart-Computer in
scripts and functions.
Examples
Example 1: Restart the local computer
Restart-Computer restarts the local computer.
Restart-Computer
Example 2: Restart multiple computers
Restart-Computer can restart remote and local computers. The ComputerName parameter accepts an
array of computer names.
Restart-Computer -ComputerName Server01, Server02, localhost
Example 3: Get computer names from a text file
Restart-Computer gets a list of computer names from a text file and restarts the computers. The
ComputerName parameter isn't specified. But because it's the first position parameter, it
accepts the computer names from the text file that are sent down the pipeline.
Get-Content -Path C:\Domain01.txt | Restart-Computer
Get-Content uses the Path parameter to get a list of computer names from a text file,
Domain01.txt. The computer names are sent down the pipeline. Restart-Computer restarts each
computer.
Example 4: Force restart of computers listed in a text file
This example forces an immediate restart of the computers listed in the Domain01.txt file.
The computer names from the text file are stored in a variable. The Force parameter forces an
immediate restart.
$Names = Get-Content -Path C:\Domain01.txt
$Creds = Get-Credential
Restart-Computer -ComputerName $Names -Credential $Creds -Force
Get-Content uses the Path parameter to get a list of computer names from a text file,
Domain01.txt. The computer names are stored in the variable $Names. Get-Credential prompts
you for a username and password and stores the values in the variable $Creds.
Restart-Computer uses the ComputerName and Credential parameters with their variables. The Force
parameter causes an immediate restart of each computer.
Example 6: Restart a remote computer and wait for PowerShell
Restart-Computer restarts the remote computer and then waits up to 5 minutes (300 seconds)
for PowerShell to become available on the restarted computer before it continues.
Restart-Computer -ComputerName Server01 -Wait -For PowerShell -Timeout 300 -Delay 2
Restart-Computer uses the ComputerName parameter to specify Server01. The Wait
parameter waits for the restart to finish. The For specifies that PowerShell can run commands on
the remote computer. The Timeout parameter specifies a five-minute wait. The Delay parameter
queries the remote computer every two seconds to determine whether it's restarted.
-------------------------------------------------------------------------------------------
Stop-Computer
Stops (shuts down) local and remote computers.
Syntax
Stop-Computer
[-WsmanAuthentication ]
[[-ComputerName] ]
[[-Credential] ]
[-Force]
[-WhatIf]
[-Confirm]
[]
Description
The Stop-Computer cmdlet shuts down the local computer and remote computers.
You can use the parameters of Stop-Computer to specify the authentication levels and alternate
credentials, and to force an immediate shut down.
Examples
Example 1: Shut down the local computer
This example shuts down the local computer.
Stop-Computer -ComputerName localhost
Example 2: Shut down two remote computers and the local computer
This example stops two remote computers and the local computer.
Stop-Computer -ComputerName "Server01", "Server02", "localhost"
Stop-Computer uses the ComputerName parameter to specify two remote computers and the local
computer. Each computer is shut down.
Example 3: Shut down remote computers as a background job
In this example, Stop-Computer runs as a background job on two remote computers.
The background operator & runs the Stop-Computer command as a background job. For more
information, see about_Operators.
$j = Stop-Computer -ComputerName "Server01", "Server02" &
$results = $j | Receive-Job
$results
Stop-Computer uses the ComputerName parameter to specify two remote computers. The &
background operator runs the command as a background job. The job objects are stored in the $j
variable.
The job objects in the $j variable are sent down the pipeline to Receive-Job, which gets the job
results. The objects are stored in the $results variable. The $results variable displays the job
information in the PowerShell console.
Example 4: Shut down a remote computer
This example shuts down a remote computer using specified authentication.
Stop-Computer -ComputerName "Server01" -WsmanAuthentication Kerberos
Stop-Computer uses the ComputerName parameter to specify the remote computer. The
WsmanAuthentication parameter specifies to use Kerberos to establish a remote connection.
Example 5: Shut down computers in a domain
In this example, the commands force an immediate shut down of all computers in a specified domain.
$s = Get-Content -Path ./Domain01.txt
$c = Get-Credential -Credential Domain01\Admin01
Stop-Computer -ComputerName $s -Force -Credential $c
Get-Content uses the Path parameter to get a file in the current directory with the list of
domain computers. The objects are stored in the $s variable.
Get-Credential uses the Credential parameter to specify the credentials of a domain
administrator. The credentials are stored in the $c variable.
Stop-Computer shuts down the computers specified with the ComputerName parameter's list of
computers in the $s variable. The Force parameter forces an immediate shutdown. The
Credential parameter submits the credentials saved in the $c variable.
-------------------------------------------------------------------------------------------
Start-Service
Syntax
Start-Service
[-InputObject]
[-PassThru]
[-Include ]
[-Exclude ]
[-WhatIf]
[-Confirm]
[]
Start-Service
[-Name]
[-PassThru]
[-Include ]
[-Exclude ]
[-WhatIf]
[-Confirm]
[]
Start-Service
[-PassThru]
-DisplayName
[-Include ]
[-Exclude ]
[-WhatIf]
[-Confirm]
[]
Description
The Start-Service cmdlet sends a start message to the Windows Service Controller for each of the
specified services. If a service is already running, the message is ignored without error. You can
specify the services by their service names or display names, or you can use the InputObject
parameter to supply a service object that represents the services that you want to start.
Examples
Example 1: Start a service by using its name
This example starts the EventLog service on the local computer. The Name parameter identifies
the service by its service name.
Start-Service -Name "eventlog"
Example 2: Display information without starting a service
This example shows what would occur if you started the services that have a display name that
includes "remote".
Start-Service -DisplayName *remote* -WhatIf
The DisplayName parameter identifies the services by their display name instead of their service
name. The WhatIf parameter causes the cmdlet to display what would happen when you run the
command but does not make changes.
Example 3: Start a service and record the action in a text file
This example starts the Windows Management Instrumentation (WMI) service on the computer and adds a
record of the action to the services.txt file.
$s = Get-Service wmi
Start-Service -InputObject $s -PassThru | Format-List >> services.txt
First we use Get-Service to get an object that represent the WMI service and store it in the $s
variable. Next, we start the service. Without the PassThru parameter, Start-Service does not
create any output. The pipeline operator (|) passes the object output by Start-Service to the
Format-List cmdlet to format the object as a list of its properties. The append redirection
operator (>>) redirects the output to the services.txt file. The output is added to the end of the
existing file.
Example 4: Start a disabled service
This example shows how to start a service when the start type of the service is Disabled.
PS> Start-Service tlntsvr
Start-Service : Service 'Telnet (TlntSvr)' cannot be started due to the following error: Cannot start service TlntSvr on computer '.'.
At line:1 char:14
+ Start-Service <<<< tlntsvr
PS> Get-CimInstance win32_service | Where-Object Name -eq "tlntsvr"
ExitCode : 0
Name : TlntSvr
ProcessId : 0
StartMode : Disabled
State : Stopped
Status : OK
PS> Set-Service tlntsvr -StartupType manual
PS> Start-Service tlntsvr
The first attempt to start the Telnet service (tlntsvr) fails. The Get-CimInstance command shows
that the StartMode property of the Tlntsvr service is Disabled. The Set-Service cmdlet
changes the start type to Manual. Now, we can resubmit the Start-Service command. This time,
the command succeeds. To verify that the command succeeded, run Get-Service.
------------------------------------------------------------------------------------------
Start-Process
Starts one or more processes on the local computer.
Syntax
Start-Process
[-FilePath]
[[-ArgumentList] ]
[-Credential ]
[-WorkingDirectory ]
[-LoadUserProfile]
[-NoNewWindow]
[-PassThru]
[-RedirectStandardError ]
[-RedirectStandardInput ]
[-RedirectStandardOutput ]
[-WindowStyle ]
[-Wait]
[-UseNewEnvironment]
[-WhatIf]
[-Confirm]
[]
Start-Process
[-FilePath]
[[-ArgumentList] ]
[-WorkingDirectory ]
[-PassThru]
[-Verb ]
[-WindowStyle ]
[-Wait]
[-WhatIf]
[-Confirm]
[]
Description
The Start-Process cmdlet starts one or more processes on the local computer. By default,
Start-Process creates a new process that inherits all the environment variables that are defined
in the current process.
To specify the program that runs in the process, enter an executable file or script file, or a file
that can be opened by using a program on the computer. If you specify a non-executable file,
Start-Process starts the program that is associated with the file, similar to the Invoke-Item
cmdlet.
You can use the parameters of Start-Process to specify options, such as loading a user profile,
starting the process in a new window, or using alternate credentials.
Examples
Example 1: Start a process that uses default values
This example starts a process that uses the Sort.exe file in the current folder. The command uses
all of the default values, including the default window style, working folder, and credentials.
Start-Process -FilePath "sort.exe"
Example 2: Print a text file
This example starts a process that prints the C:\PS-Test\MyFile.txt file.
Start-Process -FilePath "myfile.txt" -WorkingDirectory "C:\PS-Test" -Verb Print
Example 3: Start a process to sort items to a new file
This example starts a process that sorts items in the Testsort.txt file and returns the sorted
items in the Sorted.txt files. Any errors are written to the SortError.txt file.
Start-Process -FilePath "Sort.exe" -RedirectStandardInput "Testsort.txt" -RedirectStandardOutput "Sorted.txt" -RedirectStandardError "SortError.txt" -UseNewEnvironment
The UseNewEnvironment parameter specifies that the process runs with its own environment
variables.
Example 4: Start a process in a maximized window
This example starts the Notepad.exe process. It maximizes the window and retains the window until
the process completes.
Start-Process -FilePath "notepad" -Wait -WindowStyle Maximized
Example 5: Start PowerShell as an administrator
This example starts PowerShell by using the Run as administrator option.
Start-Process -FilePath "powershell" -Verb RunAs
Example 6: Using different verbs to start a process
This example shows how to find the verbs that can be used when starting a process. The available
verbs are determined by the filename extension of the file that runs in the process.
$startExe = New-Object System.Diagnostics.ProcessStartInfo -Args PowerShell.exe
$startExe.verbs
open
runas
runasuser
The example uses New-Object to create a System.Diagnostics.ProcessStartInfo object for
PowerShell.exe, the file that runs in the PowerShell process. The Verbs property of the
ProcessStartInfo object shows that you can use the Open and RunAs verbs with
PowerShell.exe, or with any process that runs a .exe file.
Example 7: Specifying arguments to the process
Both commands start the Windows command interpreter, issuing a dir command on the Program Files
folder. Because this foldername contains a space, the value needs surrounded with escaped quotes.
Note that the first command specifies a string as ArgumentList. The second command a string
array.
Start-Process -FilePath "$env:comspec" -ArgumentList "/c dir `"%systemdrive%\program files`""
Start-Process -FilePath "$env:comspec" -ArgumentList "/c","dir","`"%systemdrive%\program files`""
--------------------------------------------------------------------------------------------
Rename-Computer
Syntax
Rename-Computer
[-ComputerName ]
[-PassThru]
[-DomainCredential ]
[-LocalCredential ]
[-NewName]
[-Force]
[-Restart]
[-WsmanAuthentication ]
[-WhatIf]
[-Confirm]
[]
Description
The Rename-Computer cmdlet renames the local computer or a remote computer.
It renames one computer in each command.
This cmdlet was introduced in Windows PowerShell 3.0.
Examples
Example 1: Rename the local computer
This command renames the local computer to Server044 and then restarts it to make the change
effective.
Rename-Computer -NewName "Server044" -DomainCredential Domain01\Admin01 -Restart
Example 2: Rename a remote computer
This command renames the Srv01 computer to Server001. The computer is not restarted.
The DomainCredential parameter specifies the credentials of a user who has permission to rename
computers in the domain.
The Force parameter suppresses the confirmation prompt.
Rename-Computer -ComputerName "Srv01" -NewName "Server001" -DomainCredential Domain01\Admin01 -Force
------------------------------------------------------------------------------------------









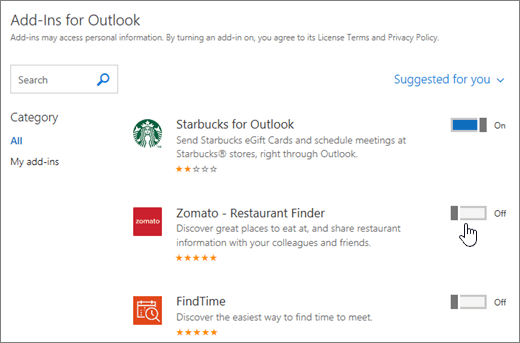
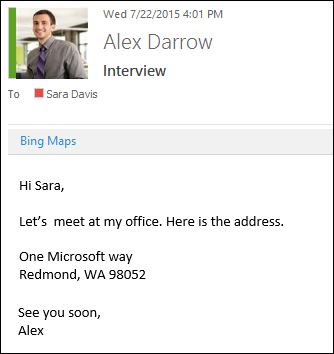
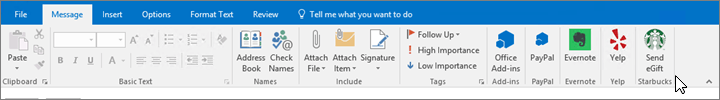
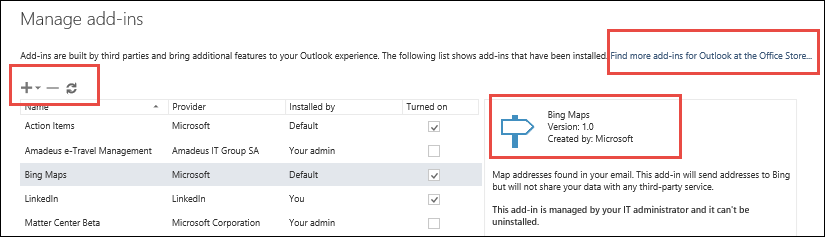
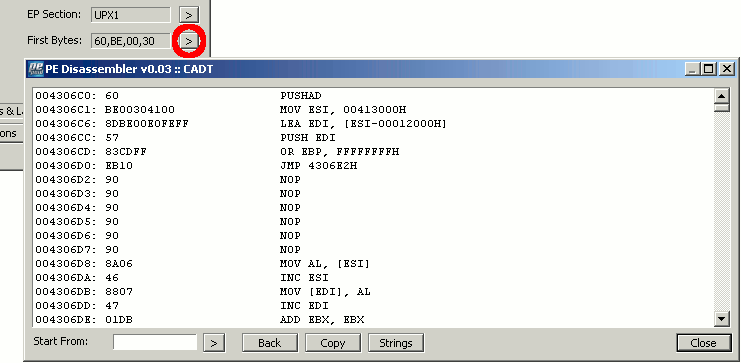
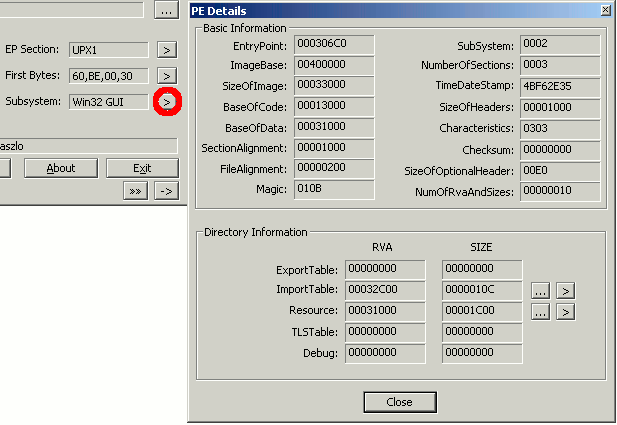
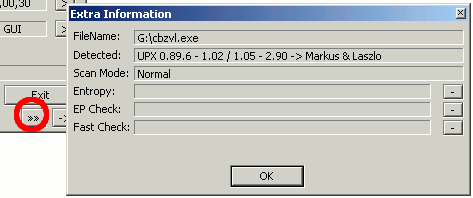
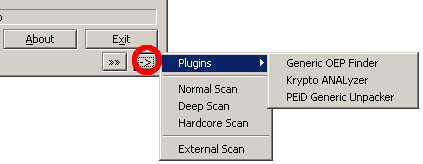
 > Manage integrations.
> Manage integrations.









![Abu Dhabi Police GHQ virus [Image: Abu Dhabi Police GHQ lock screen virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/04/Abu-Dhabi-Police-GHQ-virus.jpg)
![[Image: Safe Mode with Networking]](https://malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)
![Type msconfig in the Command prompt [Image: Type msconfig in the Command prompt]](https://malwaretips.com/blogs/wp-content/uploads/2013/02/command-prompt-start-msconfig.jpg)
![Uncheck any suspicious entries from start-up [Image: Uncheck any suspicious entries from start-up]](https://malwaretips.com/blogs/wp-content/uploads/2013/02/msconfig-remove-startup-item.jpg)
![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](https://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](https://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)
![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](https://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)