After installing VMware vCenter Server Appliance (VCSA) 6.5, we only have a "vSphere.local" single sign-on (SSO) domain where we can create users and groups. But wouldn't it be better if you could integrate your existing Microsoft Active Directory (AD) environment with your organizational structure of groups and users? You don't have to start over creating these just for VMware. We just need to link the AD environment to the VMware SSO.
We also have to grant some permissions to the enterprise AD administrator, otherwise, he or she will not be able to manage the environment.
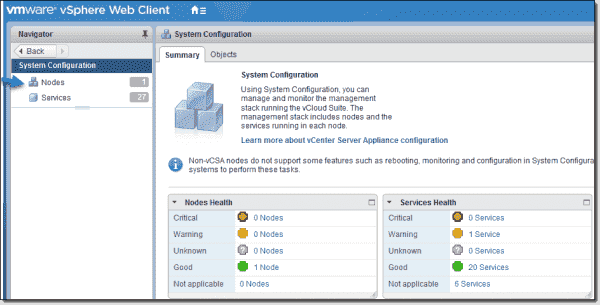
I assume that you have already fired up the vSphere web client and logged in using the administrator@vsphere.local account and password we set up in our previous post. Once done, click the System Configuration button on the main screen. You'll end up in the System Configuration section. Click the Nodes section on the left.
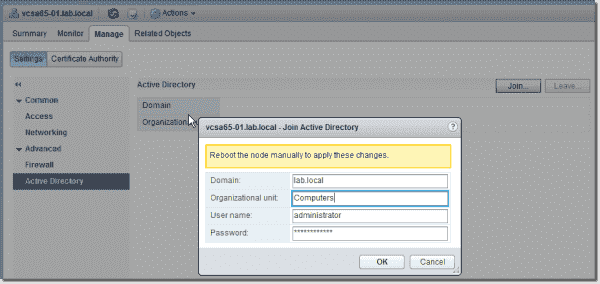
All nodes will appear below. As we have only a single node (we're not using vCenter's linked mode), select the node > Manage tab > Active Directory > Join button.
Enter the necessary details. As you can see, a message says you have to reboot the node manually.
After the reboot, you'll have to wait a few minutes until all services are up and the vSphere web client initializes itself.
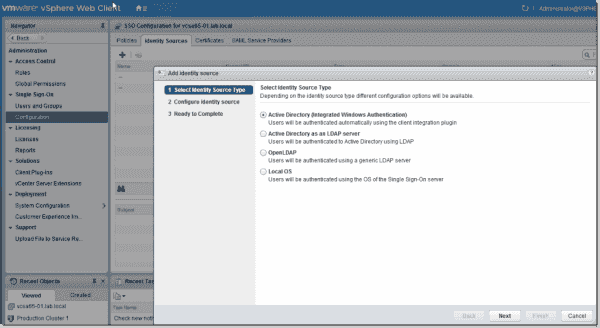
Log back in, and from the main screen, click the Home button and Administration. Under Single Sign-On, select the Configuration menu, the Identity Source tab and then click the green + sign to Add identity source.
Four options appear. We'll stick with Active Directory (Integrated Windows Authentication).
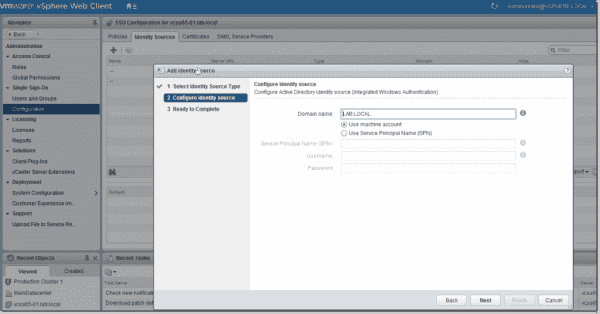
On the next page, the domain should already display with the Use machine account radio button pre-selected.
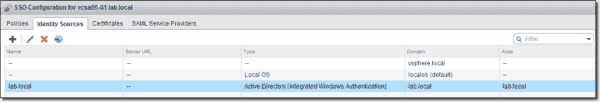
Click the Next button and then Finish. You should see the Identity Sources tab populated with your Active Directory.
As mentioned at the beginning, we'll need to grant a few permissions for the domain administrator (or any other account) to manage the vSphere environment.
On the same page, move one level up to the Access control section and select Global Permissions.
Click Add a new user and then select the user from the Active Directory.
Next, validate by clicking the OK button.
This is just first part of the procedure. We still have to add the domain administrator to some vSphere.local groups. We'll do that in a second.
Select Users and Groups > Groups tab > Administrators. Add the domain admin account to the local administrators group.
Click the Add button and validate with the OK button. Repeat the procedure for ComponentManager.Administrators, LicenseService.Administrators, CAAdmins, SystemConfiguration.Administrators, SystemConfiguration.BashShellAdministrators and Users.
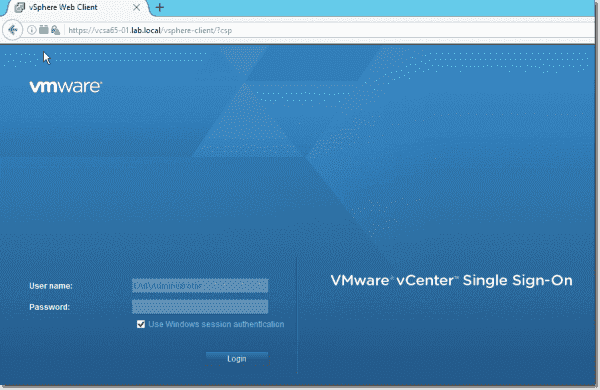
You should now be able to log in as a domain admin. And if you're already logged in as a domain admin on your system, you can simply check the box to Use Windows session authentication.
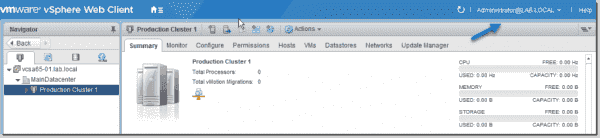
You can then see in the top right corner that you have logged in as domain admin.
We also have to grant some permissions to the enterprise AD administrator, otherwise, he or she will not be able to manage the environment.
I assume that you have already fired up the vSphere web client and logged in using the administrator@vsphere.local account and password we set up in our previous post. Once done, click the System Configuration button on the main screen. You'll end up in the System Configuration section. Click the Nodes section on the left.
All nodes will appear below. As we have only a single node (we're not using vCenter's linked mode), select the node > Manage tab > Active Directory > Join button.
Enter the necessary details. As you can see, a message says you have to reboot the node manually.
After the reboot, you'll have to wait a few minutes until all services are up and the vSphere web client initializes itself.
Log back in, and from the main screen, click the Home button and Administration. Under Single Sign-On, select the Configuration menu, the Identity Source tab and then click the green + sign to Add identity source.
Four options appear. We'll stick with Active Directory (Integrated Windows Authentication).
On the next page, the domain should already display with the Use machine account radio button pre-selected.
Click the Next button and then Finish. You should see the Identity Sources tab populated with your Active Directory.
As mentioned at the beginning, we'll need to grant a few permissions for the domain administrator (or any other account) to manage the vSphere environment.
On the same page, move one level up to the Access control section and select Global Permissions.
Click Add a new user and then select the user from the Active Directory.
Next, validate by clicking the OK button.
This is just first part of the procedure. We still have to add the domain administrator to some vSphere.local groups. We'll do that in a second.
Select Users and Groups > Groups tab > Administrators. Add the domain admin account to the local administrators group.
Click the Add button and validate with the OK button. Repeat the procedure for ComponentManager.Administrators, LicenseService.Administrators, CAAdmins, SystemConfiguration.Administrators, SystemConfiguration.BashShellAdministrators and Users.
You should now be able to log in as a domain admin. And if you're already logged in as a domain admin on your system, you can simply check the box to Use Windows session authentication.
You can then see in the top right corner that you have logged in as domain admin.



The OneSimCard M2M Worldwide IoT SIM Card is a fabulous fit for wearables because it offers premium around-the-world M2M administrations with over 325 organized wandering partners.
ReplyDelete