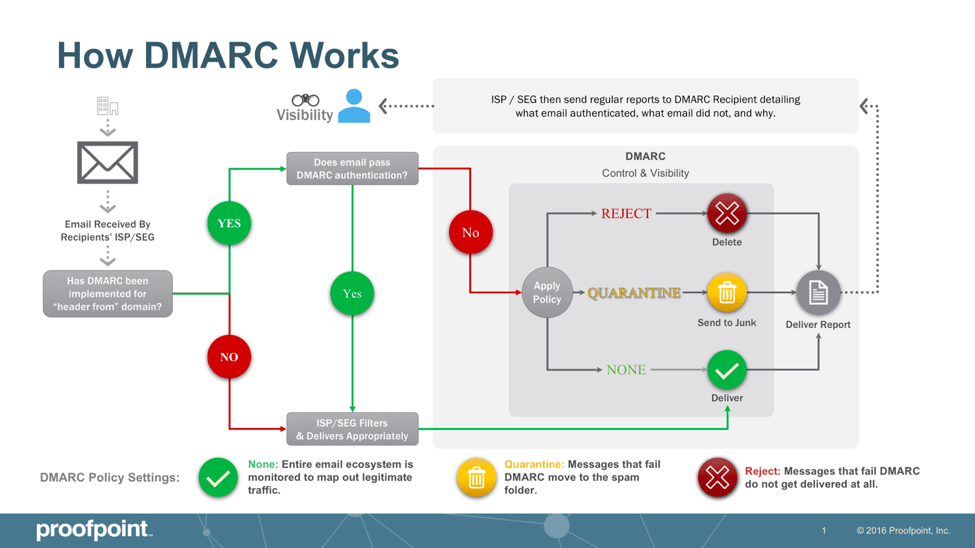
For a message to pass DMARC authentication, it must pass SPF authentication and SPF alignment and/or pass DKIM authentication and DKIM alignment. If a message fails DMARC, senders can instruct receivers on what to do with that message via a DMARC policy. There are three DMARC policies the domain owner can enforce: none (the message is delivered to the recipient, and the DMARC report is sent to the domain owner), quarantine (the message is moved to a quarantine folder) and reject (the message is not delivered at all).
The DMARC policy of “none” is a good first step. This way, the domain owner can ensure that all legitimate emails authenticate properly. The domain owner receives DMARC reports to help ensure that all legitimate email is identified and passes authentication. Once the domain owner is confident they have identified all legitimate senders and have fixed authentication issues, they can move to a policy of “reject” and block phishing, business email compromise, and other email fraud attacks. As an email receiver, an organization can ensure that its secure email gateway enforces the DMARC policy implemented by the domain owner. This will protect employees against inbound email threats.
SPF authentication starts by identifying all legitimate IP addresses that should send email from a given domain and then publishes this list in the DNS. Before delivering a message, email providers verify the SPF record by looking up the domain included in the “envelope from” address within the hidden technical header of the email. If the IP address sending an email on behalf of this domain is not listed in the domain’s SPF record, the message fails SPF authentication.
For DKIM authentication, the sender first identifies what fields they want to include in their DKIM signature, such as the “from” address, the body of the email, the subject, and more. These fields must remain unchanged in transit, or the message will fail DKIM authentication. The sender’s email platform will create a hash of the text fields included in the DKIM signature. Once the hash string is generated, it is encrypted with a private key only the sender can access. After the email is sent, it’s up to the email gateway or consumer mailbox provider to validate the DKIM signature by locating a public key that matches the private key. Then the DKIM signature is decrypted back to its original hash string.
Benefits of DMARC
DMARC provides several benefits in reinforcing email-based cybersecurity measures for organizations that implement it. Some of the core advantages of leveraging DMARC include:
Improves email deliverability: Setting a DMARC record in your DNS settings can improve overall email deliverability while preventing threat actors from delivering malicious emails using your domain.
Lowers the risk of email phishing attacks: DMARC effectively prevents and mitigates the risk of phishing attacks, which can be costly to an organization and its bottom line.
Enforces sender policies: DMARC allows organizations to enforce policies via its DNS record, defining specific practices for email authentication and providing instructions for receiving mail servers about how to enforce them.
Protects brand reputation: DMARC helps protect an organization’s brand reputation by preventing cybercriminals from impersonating their domain and deceiving customers and clients into releasing sensitive information.
Provides thorough authentication reporting: DMARC checks can help support an organization’s email system by offering comprehensive authentication reporting.
Functions at scale: DMARC is intended to perform with internet scalability, making it an effective tool for large-scale organizations, institutions, and corporate entities.
While many of these benefits overlap, the underlying function of DMARC is to better protect email through effective authentication and threat mitigation.
DMARC Best Practices and Tools
Due to the volume of DMARC reports that an email sender can receive and the lack of clarity provided within DMARC reports, fully implementing DMARC authentication can be difficult. These tools and best practices can help ensure your organization optimizes DMARC.
Publish policies to your DNS record that clearly define your organization’s practices for email authentication and document instructions for receiving mail servers about how to enforce those policies.
DMARC parsing tools can help organizations understand the information in DMARC reports.
Additional data and insights beyond what’s included within DMARC reports help organizations identify email senders faster and more accurately. This helps speed up the implementation of DMARC authentication and reduces the risk of blocking legitimate email.
Professional service consultants with DMARC expertise can help organizations with DMARC implementation. Consultants help identify all legitimate senders, fix authentication issues, and even work with email service providers to ensure they authenticate properly.
Organizations can create a DMARC record in minutes and start gaining visibility through DMARC reports by enforcing a DMARC policy of “none.”
By properly identifying all legitimate email senders-–including third-party email service providers—and fixing any authentication issues, organizations should reach a high confidence level before enforcing a DMARC policy of “reject.”
DMARC implementation can be complicated, but it’s a critical protocol in securing your organization’s email channels and mitigating fraudulent activity.
How to Create a DMARC Record
Implementing DMARC is a powerful solution to protect your email against impostors and fraudulent activity. Creating a DMARC record is the first step to protecting your organization, customers, and brand reputation from email fraud. You can use Proofpoint’s DMARC Creation Wizard to create a record for your organization or follow the steps below to get started.
DMARC records are hosted on your DNS servers as TXT entries. Every host provider grants DNS access to customers, so you can add this TXT entry from the registrar where the domain was registered or in a dashboard provided by the website host. The steps to create a DMARC record differ based on the registrar or host, but creating the record is the same for every domain. After you authenticate into your host or registrar, create a DNS entry using the following steps:
Create a TXT record. After you start the creation process, you must enter a name and value for the record.
Name your record “DMARC.” In some host configurations, the domain name is automatically appended to the name. If it is not added automatically, name the record _dmarc.yourdomain.com.
Enter the value for your record. The following is an example value for DMARC:
v=DMARC1; p=none; rua=mailto:youraddress@yourdomain.com.
The three values in the entry are critical for direction when users send emails to your domain. The first “v” value is necessary and defines the version. This value will be the same for all records. The second “p” value determines what happens when the email passes or fails. In this example, the value is set to “none,” indicating nothing will happen. This value is recommended initially to ensure that DMARC works correctly before quarantining messages.
After you verify that DMARC works correctly, the “p” value can be changed to “quarantine” or “reject.” It’s recommended to quarantine messages so that you can catch false positives. The message will be set aside until you review it. The “reject” option will outright drop records that don’t pass DMARC rules. Only use the “reject” option when you are positive that no important messages will be dropped by your DMARC settings.


